Malicious Chrome extensions have been known to find their way into the Chrome Web Store all the time.
In fact, there have been reports of dangerous extensions from Chrome affecting approximately 1.4 million users worldwide.
Luckily, you can take a few steps to get rid of them. We will discuss them here in this article.
What are malicious Chrome extensions?
Malicious Chrome extensions, also known as malware, are add-ons that contain dangerous codes that execute commands on your system without your approval.
They aim to penetrate, harm, or impair computers, computer systems, networks, tablets, and mobile devices.
They frequently do this by gaining control over your device’s activities.
Nasty, vile, intrusive, and hostile, malicious Chrome extensions are used for various reasons.
They may be used to make money from or off of you and even hinder your capacity to do tasks.
They may also make a political statement, frame you, or simply intrude on you and brag about it.
Although they can’t physically harm your computer, they can steal, encrypt, or delete your data.
They can also change or hijack essential computer operations and spy on your activities online.
Can you get a virus from a Chrome extension?
The answer is yes. Due to these extensions’ extensive access, software policies may pop up telling you there are new updates.
Since the average user doesn’t care to read software policies, a virus may be introduced into an existing extension that was previously safe from malware.
This is especially so if you didn’t add the extension via the Chrome Web Store.
How to tell if there are malicious Chrome extensions
1. You lose access to your computer or your files
If you discover that your computer has begun doing some kinds of stuff that you didn’t authorize, it’s probably due to a malicious Chrome extension.
Usually, hackers announce themselves by changing the wallpaper of your system or your home screen to theirs.
This is their way of informing you that they’re in control of your system and may demand ransom to disinfect your computer.
2. Your computer is running slow
One of the consequences of malicious Chrome extensions is that they reduce the speed of your operating system.
If you notice the fan of your computer whirring unusually at full speed, it may be a sign that there are ongoing background actions you’re unaware of.
This sometimes happens when your computer is trapped in the botnet, a network of computers that blast out spam, perform malicious network attacks, or even mine cryptocurrency.
3. Pop-ups intrude on your computer
If it becomes normal for you to get pop-ups and unsolicited ads, it might be a sign that your browser has been infected by a general malware or a malicious Chrome extension.
So, simply ignore these pop-ups and remove the extensions as quickly as you can.
4. There is an unusual increase in your internet activity
Let’s illustrate how this scenario can manifest with Trojans. Trojans are one of the ways in which malware works.
Once it lands on your computer and becomes active, the next thing they do is try to communicate with the attacker’s command and control server to download secondary infections. This explains the spike in your internet activity.
5. Your anti-virus gets deactivated suddenly
If your anti-virus stops working after you added a Chrome Extension and you cannot turn it back on, it’s a sign that the extension is probably malware.
6. Your system crashes, or your browser freezes
When you unknowingly install a malicious Chrome extension, it might cause your system to start crashing. It might also cause your browser to freeze even when you don’t open multiple tabs.
7. Your browser setting has changed
When you click on one of those nasty pop-ups from malicious Chrome extensions, they sometimes download additional software.
This new software may infest your system and change your settings.
8. You’re losing disk space
If you notice your hard disk decreasing in storage space drastically without downloading anything that may impact that, it’s a sign that your computer is going through a malware attack.
How to avoid malicious Chrome extensions
Given how malicious Chrome extensions affect your computer, you must learn how to protect yourself against them.
Here are the ways to avoid them:
- Install only extensions that are policy-compliant and hosted on trusted sources or on Google Chrome. Chrome Web Store’s policies say extensions must not be active by default.
- Extensions must first ask your permission to enable them within Chrome. They cannot disable Chrome dialogues that notify users of changes in their settings.
- Be wary of offers that seem too good to be true. It’s not uncommon for malware to be downloaded by promising you the chance to win a contest or giving you free access to expensive copyrighted content.
- Ignore fake warnings and clickbait. You should take unfounded warnings about a viral infection on your device with a pinch of salt. The idea here is to scare you into downloading unwanted software or extensions from their website.
- Check the notification pop-ups from an extension after you added one. This applies even if you download it from the Chrome Web Store.
- If you don’t trust what the software will do on your system, uninstall it without delay.
- Enhance your protection level when using Chrome’s Safe Browsing features.
- Don’t click on a pop-up asking you to update or download an application if it seems fishy. Visit the program’s official website instead to get more information about it.
- Before adding an extension, make sure that it contains a seamless uninstallation flow.
The list is inexhaustible. But these are the general rules of thumb to be safe from malware.
How do I get rid of malicious Chrome extensions?
Let’s say you followed all the preventive methods, yet your computer still gets infected. How do you resolve that?
In this case, you may use Chrome to discover shady or undesirable software on your PC.
Simply remove any identified malicious Chrome extension, and Chrome will uninstall it.
How to check Chrome for malware
To be able to identify a malicious extension for removal, run a Safety Check as follows:
Step 1
Copy and paste this chrome://settings/safetyCheck. in your Chrome browser’s address bar.
The following notification should show up, as you’ll see in the image below:
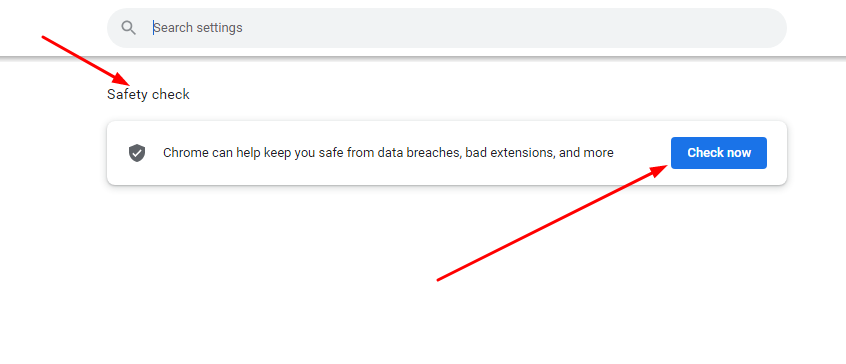
Step 2
Next, click the blue icon that says “Check Now”.
After identifying malicious software, click on the three dots in the upper right corner of your Chrome browser.
Scroll to “More Tools”, then scroll to “Extensions.”
Remove the particular malicious extension that Chrome identified during your safety check.
Note, however, that merely removing malicious Chrome extensions may not solve the problem.
In this case, you need to look at step 3.
Step 3
Manually clean your browser to eliminate the malware.
- First, launch your Chrome browser.
- Next, click the three dots in the top right corner.,
- Next, click on “Settings”.
- Next, click “Advanced” in the bottom section if you see it. Otherwise, implement the next step.
- Select the “Reset and Clean Up” menu.
- Next, select “Clean Up Computer” and select “Find.” Or you can directly copy and paste chrome://settings/cleanup to your Chrome browser. It’ll take you to the location shown in the image below.
- Wait while the browser checks for harmful software.
- Select “Delete” when asked to remove the malicious software. Afterward, reboot or restart your computer.
- If you’ve tried all of the above and still notice the same symptoms, you might need to proceed with the next section to remove all Trojan viruses and malicious software from your computer.
How to remove Trojan virus, unwanted ads, pop-ups, and other dangerous malware from your computer
Step 1
Launch your computer and go to your Windows bar.
Step 2
Search for “run” and launch the Run app. You may also launch the App by pressing the Windows key + R.
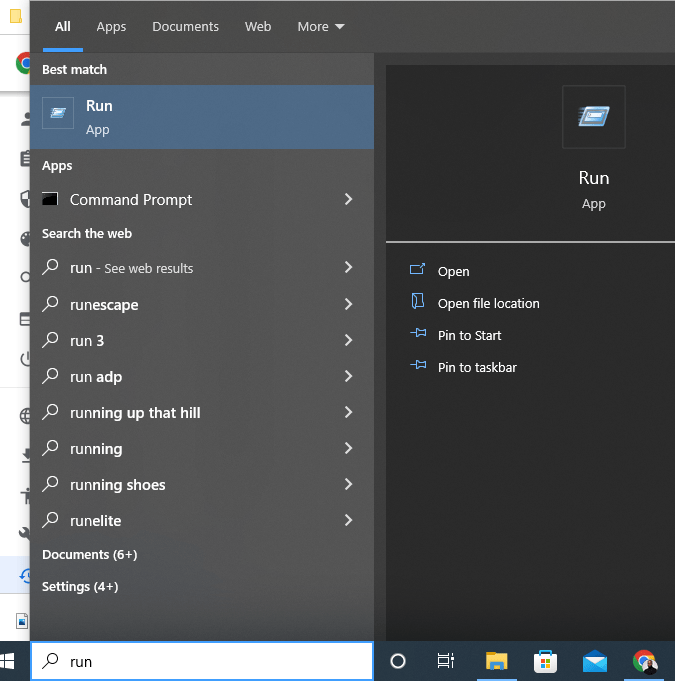
Step 3
Type “MRT” without quotation marks. Select “OK”, then select “Yes” to the Microsoft prompt that pops up.
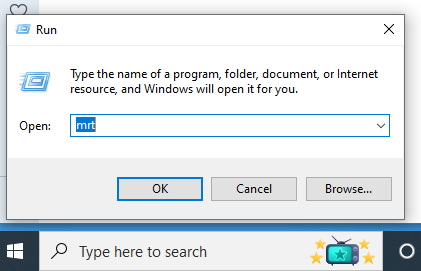
Step 4
Once you see the new window from Microsoft displaying the words “Microsoft Windows Malicious Software Removal Tool”, select “Next”.
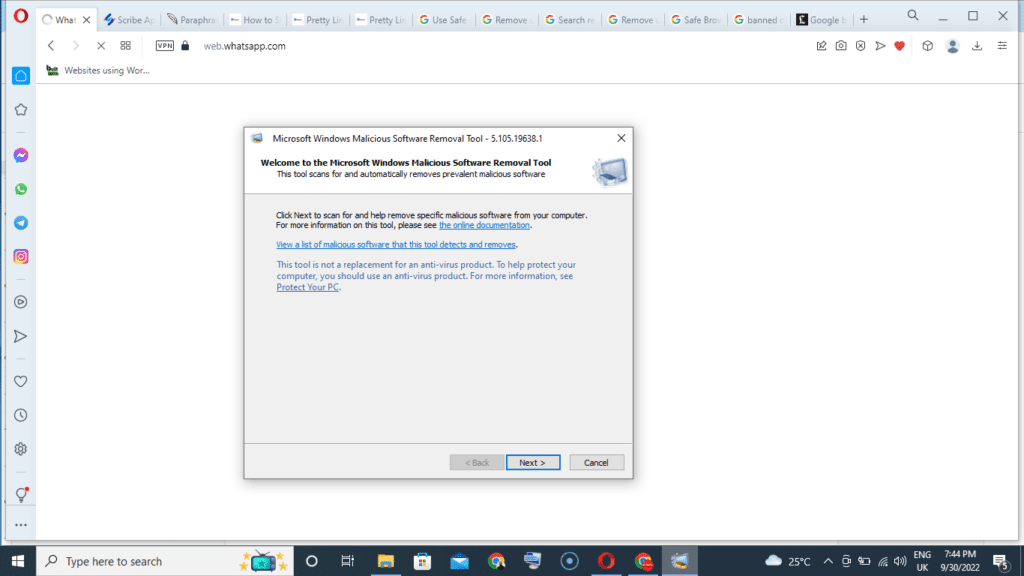
You’ll see three types of scans. Choose any of the three to allow Microsoft to check for any malicious software on your system.
This process might take anywhere between 5 minutes to 30 minutes to finish.
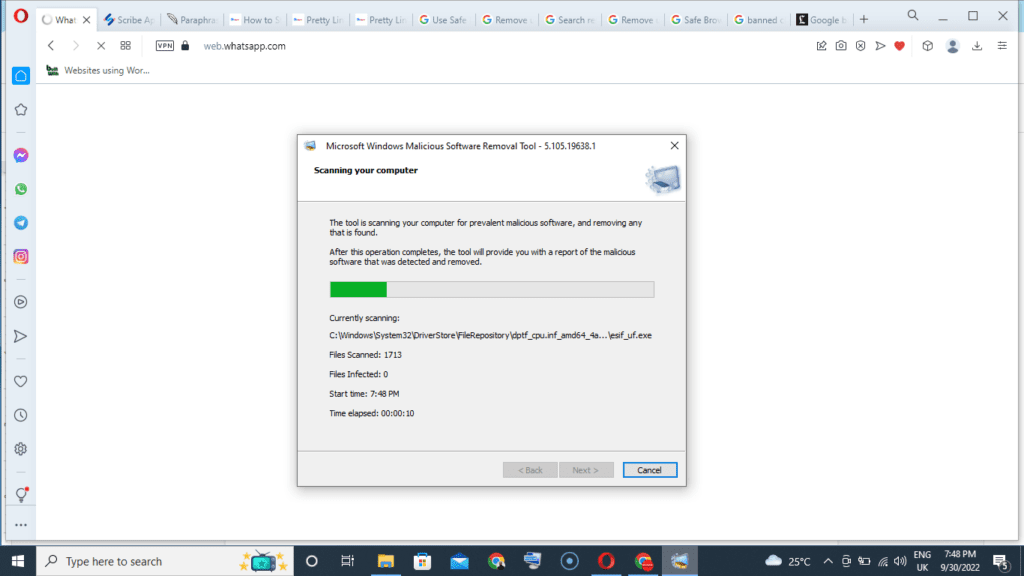
Once this process ends, you’ll see the malware or virus causing trouble on your PC.
Make sure you have Window’s Real-Time Protection set as on.
To do this, search for “Windows Security” in your Window search bar.
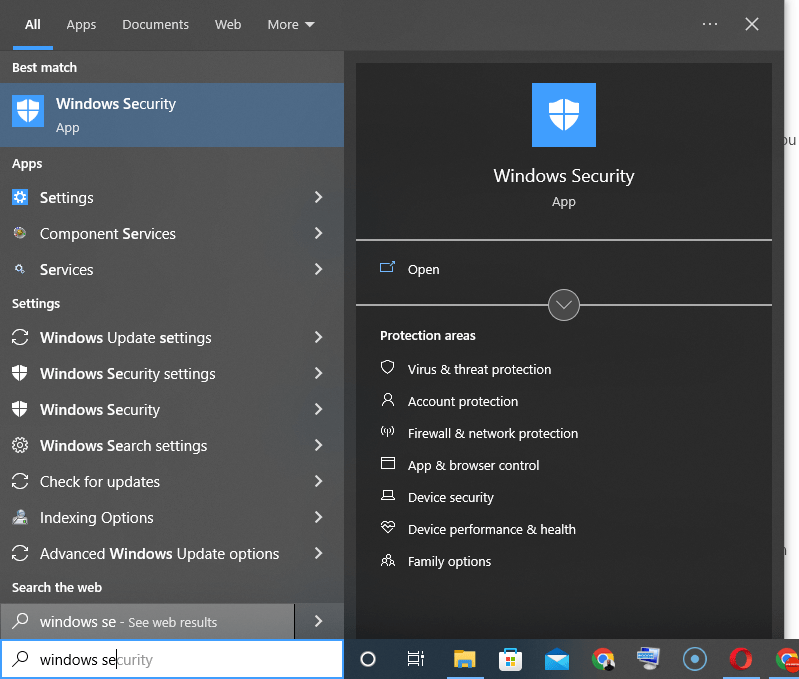
Then, select “Virus and Threat Protection”, as you’ll see below:
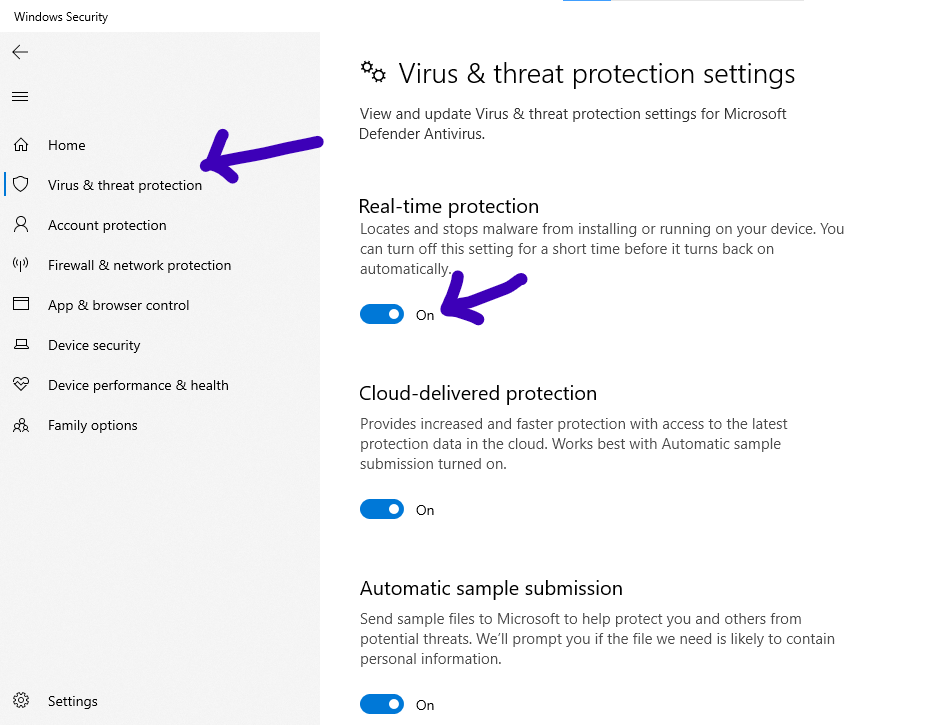
Ensure that Real-Time Protection is turned on.
List of general malicious Chrome extensions
Here are the lists of malicious Chrome extensions you should know.
1. Microsoft Authenticator
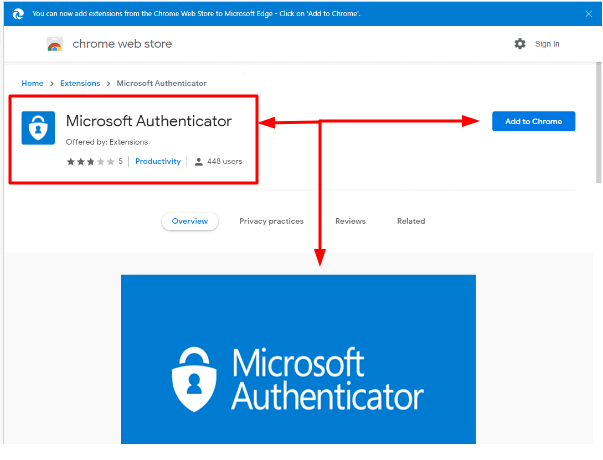
Uploaded to the Chrome Web Store on April 23, 2021, Microsoft Authenticator has positive reviews that look like they were bought.
But what truly makes it fake and harmful is its developer information that mentions a Gmail address.
The reviews also reveal a mixture of praises for the alleged extension and warnings from users who unwittingly downloaded it.
Status on Chrome Web Store: Removed by Google
2. Forcepoint Endpoint for Windows
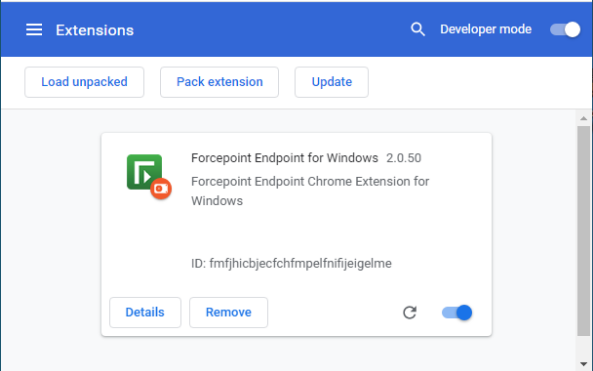
This extension abuses Chrome sync functionality to steal users’ data.
Chrome Sync is an important Chrome browser feature that allows you to synchronize data, such as bookmarks, browsing history, Apps, passwords, and other settings on your browser from one gadget to another.
It means you can access your data on two different laptops if both use the Chrome browser.
This malicious Chrome extension abused this feature before it was booted out from the Chrome Store by Google.
Status on Chrome Web Store: Removed by Google
3. uBlock Origin
This Chrome extension started as a Nano Adblocker and Nano Defender. However, its new owners rolled out new updates containing malicious codes.
The most noticeable impact that end users saw was that infected browsers automatically liked Instagram photos without user involvement.
Status on Chrome Web Store: Not yet removed by Google
Malicious Chrome extensions you should be wary of in 2022
There are five malicious Chrome extensions prevalently talked about in 2022, thanks to a McAfee security report.
Here they are in tabular form:
| Malicious Chrome Extension | Extension ID | Primary Function | Status on Chrome Web Store |
| Flipshope – Price Tracker Extension | adikhbfjdbjkhelbdnffogkobkekkkej | It automatically finds and applies coupon codes for the user with one click | The extension has been updated and corrected. It’s now safe and restored. |
| Netflix Party | mmnbenehknklpbendgmgngeaignppnbe | It allows a group of associates, family, and friends to watch Netflix movies at the same time. | Found malicious and removed by Google. It hasn’t been updated and is not safe to use. |
| Auto Buy Flash Sale | gbnahglfafmhaehbdmjedfhdmimjcbed | It allows users to buy products that are on flash sales and discounted on autopilot. | The extension has been updated and is now safe to use. As such, it’s available and live on Chrome Store. |
| Netflix Party 2 | Netflix Party 2 | It allows a group of associates, family, and friends to watch Netflix movies at the same time. | Found malicious and removed by Google. It hasn’t been updated and is not safe to use. |
| Full Page Screenshot Capture – Screenshotting | pojgkmkfincpdkdgjepkmdekcahmckjp | It’s used for taking screenshots on computers. | Found malicious and removed by Google. It hasn’t been updated and is not safe to use. |
How a malicious Chrome extension works
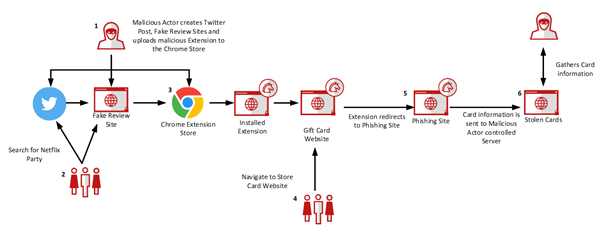
Step 1
Malicious extensions are made by the perpetrators and added to the Chrome Web Store.
Step 2
Next, they create bogus Twitter profiles and websites to deceitfully evaluate, talk about, and promote the extensions.
Step 3
A victim may stumble upon the malicious Chrome extension on the Internet, read a review, and then click a link that takes them to the Google Chrome Store.
Step 4
The user may then add the extension and agree to the permissions without knowing anything.
Step 5
While browsing online, the victim user either makes a web search or accesses an eCommerce website for purchase. As the extension already recognizes such eCommerce websites, it redirects the user to a phishing site.
Step 6
Not knowing better, the victim will input their gift card or credit card details.
Step 7
The server of that phishing site receives the sensitive details of the unsuspecting user. It then communicates the information to the owner of the malicious Chrome Extension, who may either sell the information or use the same to steal from that user.
How to verify a Chrome extension before you add them
Although Chrome extensions can be very valuable, many can be malicious and dangerous for your use.
Hence, I must share this last piece of advice to teach you how to verify an extension before you add it to your computer.
1. Do not trust anyone or anything blindly when it comes to Chrome extensions
You can only trust your due diligence when it comes to browser extensions.
After all, you just can’t trust anyone or anything regarding your online safety.
Although Google has automatic algorithms that check the safety of an extension before it’s allowed on their Web Store, these checks can still be bypassed.
In addition, extensions can get updated with new malicious codes after they have been allowed in the Web Store, so you need to be mindful at all times.
2. Check the extensions’ Privacy Policy
You will typically see this under the Privacy Practices tab.
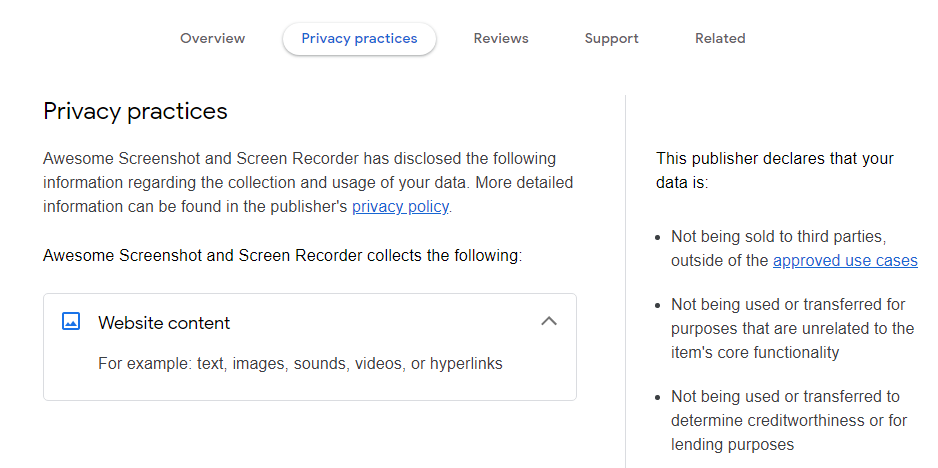
Either that, or you can check the Overview page to see the link to their policy.
In their Privacy Policy, numerous extensions that use analytics, click tracking, browser history monitoring, and other tracking forms will emphasize this fact.
Many extension authors usually bypass Google Chrome Web Store User Data Policy. So if they do, you’ll know by reading their policy.
3. Check other openly available information
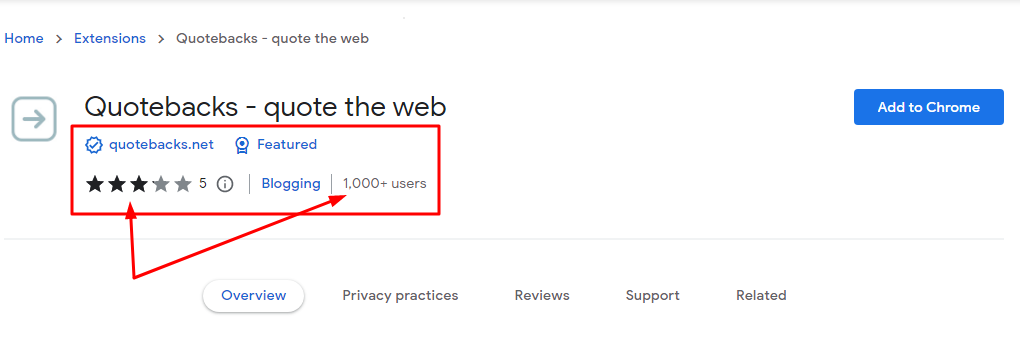
By checking the user count, reviews, and star rating, you can decide immediately if a Chrome extension is worthy or not.
You can also get other details on the extension’s profile page.
The Chrome Web Store’s profile page for the extensions shows the following details:
- The owner or developer
- The version
- Date created
- Date updated
- Size
- Language(s)
- How to contact the publisher via their email
- Their website (or Github link)
Final thoughts on malicious Chrome extensions
Although Chrome extensions can make our lives easier, this is not reason enough to throw caution in the wind and ignore the handwriting on the wall.
There are malicious Chrome extensions, and this article has done its best to enlighten you on what you need to know about them.
It’s now up to you to stay safe by using the knowledge you’ve gathered in this article.

